
whoogle Setup

In this tutorial we're going to install whoogle, a privacy frontend to browse google without any trackers.


In this tutorial we're going to install whoogle, a privacy frontend to browse google without any trackers.
git clone the repository and run the docker-compose:
[ Datura Network ] [ /dev/pts/1 ] [~]
→ cd /srv/
[ Datura Network ] [ /dev/pts/1 ] [/srv]
→ git clone https://github.com/benbusby/whoogle-search.git
Cloning into 'whoogle-search'...
remote: Enumerating objects: 4317, done.
remote: Counting objects: 100% (1088/1088), done.
remote: Compressing objects: 100% (119/119), done.
remote: Total 4317 (delta 1022), reused 997 (delta 969), pack-reused 3229
Receiving objects: 100% (4317/4317), 2.49 MiB | 14.00 MiB/s, done.
Resolving deltas: 100% (2884/2884), done.
[ Datura Network ] [ /dev/pts/1 ] [/srv]
→ cd whoogle-search
[ Datura Network ] [ /dev/pts/1 ] [/srv/whoogle-search]
→ vim docker-compose.yml
Then run the docker-compose file as it is:
[ Datura Network ] [ /dev/pts/1 ] [/srv/whoogle-search]
→ apt install docker.io docker-compose apparmor
[ Datura Network ] [ /dev/pts/1 ] [/srv/whoogle-search]
→ docker-compose up -d
Starting whoogle-search ... done
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ docker container ls -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
240a7b66aa7b benbusby/whoogle-search "/bin/sh -c 'misc/to…" 3 minutes ago Up 2 minutes (healthy) 0.0.0.0:5000->5000/tcp, :::5000->5000/tcp whoogle-search
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ nmap 127.0.0.1 -p 5000
Starting Nmap 7.93 ( https://nmap.org ) at 2023-07-15 21:20 CEST
Nmap scan report for localhost.localdomain (127.0.0.1)
Host is up (0.000095s latency).
PORT STATE SERVICE
5000/tcp open upnp
Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
once its up, put it behind the reverse nginx proxy:
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ vim whoogle.datura.network.conf
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ cat whoogle.datura.network.conf
server {
server_name whoogle.datura.network;
access_log /dev/null;
error_log /dev/null;
location / {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $host;
proxy_set_header X-NginX-Proxy true;
proxy_pass http://localhost:5000;
}
}
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ ln -s /etc/nginx/sites-available/whoogle.datura.network.conf /etc/nginx/sites-enabled
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[ Datura Network ] [ /dev/pts/1 ] [/etc/nginx/sites-available]
→ nginx -s reload
2023/07/15 21:22:46 [notice] 144766#144766: signal process started
To give make it HTTPS have the config like so:
root@Datura /etc/nginx/sites-available # cat whoogle.datura.network.conf
server {
listen 80;
listen [::]:80;
listen 443 ssl http2;
listen [::]:443 ssl http2;
######## TOR CHANGES ########
listen 4443;
listen [::]:4443;
server_name whoogle.daturab6drmkhyeia4ch5gvfc2f3wgo6bhjrv3pz6n7kxmvoznlkq4yd.onion;
add_header Onion-Location "http://whoogle.daturab6drmkhyeia4ch5gvfc2f3wgo6bhjrv3pz6n7kxmvoznlkq4yd.onion$request_uri" always;
######## TOR CHANGES ########
server_name whoogle.datura.network;
access_log off;
error_log /var/log/nginx/error.log crit;
ssl_certificate /etc/acme/certs/whoogle.datura.network/fullchain.cer;
ssl_certificate_key /etc/acme/certs/whoogle.datura.network/whoogle.datura.network.key;
access_log /dev/null;
error_log /dev/null;
location / {
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $host;
proxy_set_header X-NginX-Proxy true;
proxy_pass http://localhost:5000;
}
}
oot@Datura /etc/nginx/sites-available # systemctl stop nginx
root@Datura /etc/nginx/sites-available # acme.sh --set-default-ca --server letsencrypt
[Sat Jul 15 09:31:38 PM CEST 2023] Changed default CA to: https://acme-v02.api.letsencrypt.org/directory
root@Datura /etc/nginx/sites-available # acme.sh --issue --standalone -d whoogle.datura.network -k 4096
root@Datura /etc/nginx/sites-available # systemctl start nginx
root@Datura /etc/nginx/sites-available # systemctl status nginx
● nginx.service - A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; preset: enabled)
Active: active (running) since Sat 2023-07-15 21:32:10 CEST; 3s ago
Docs: man:nginx(8)
Process: 146558 ExecStartPre=/usr/sbin/nginx -t -q -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Process: 146559 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Main PID: 146560 (nginx)
Tasks: 13 (limit: 77000)
Memory: 9.8M
CPU: 42ms
CGroup: /system.slice/nginx.service
├─146560 "nginx: master process /usr/sbin/nginx -g daemon on; master_process on;"
├─146561 "nginx: worker process"
├─146562 "nginx: worker process"
├─146563 "nginx: worker process"
├─146564 "nginx: worker process"
├─146565 "nginx: worker process"
├─146566 "nginx: worker process"
├─146567 "nginx: worker process"
├─146568 "nginx: worker process"
├─146569 "nginx: worker process"
├─146570 "nginx: worker process"
├─146571 "nginx: worker process"
└─146572 "nginx: worker process"
Jul 15 21:32:10 Datura systemd[1]: Starting nginx.service - A high performance web server and a reverse proxy server...
Jul 15 21:32:10 Datura systemd[1]: Started nginx.service - A high performance web server and a reverse proxy server.
Once nginx restarts, just browse to your website:
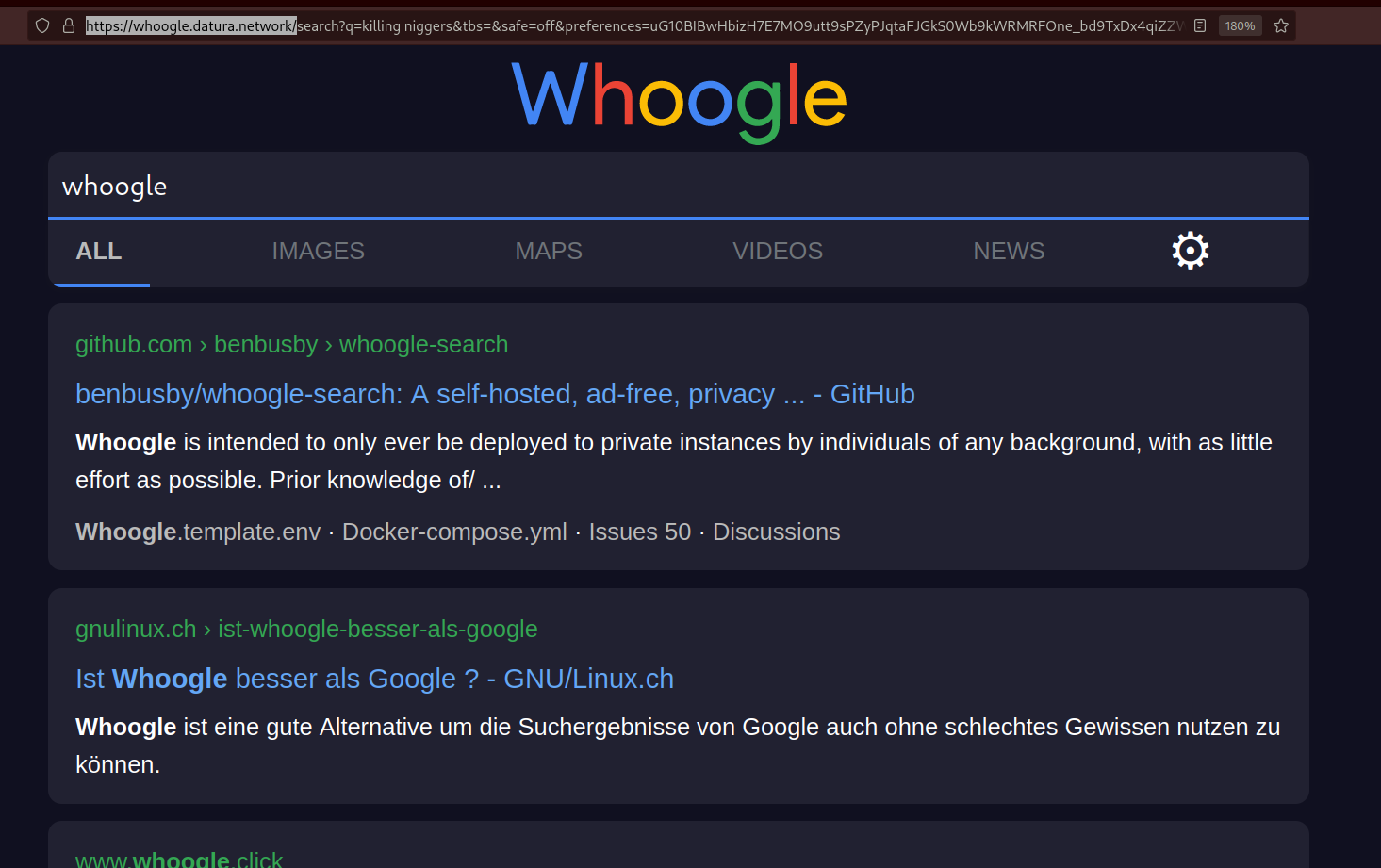
also test the onion website here:
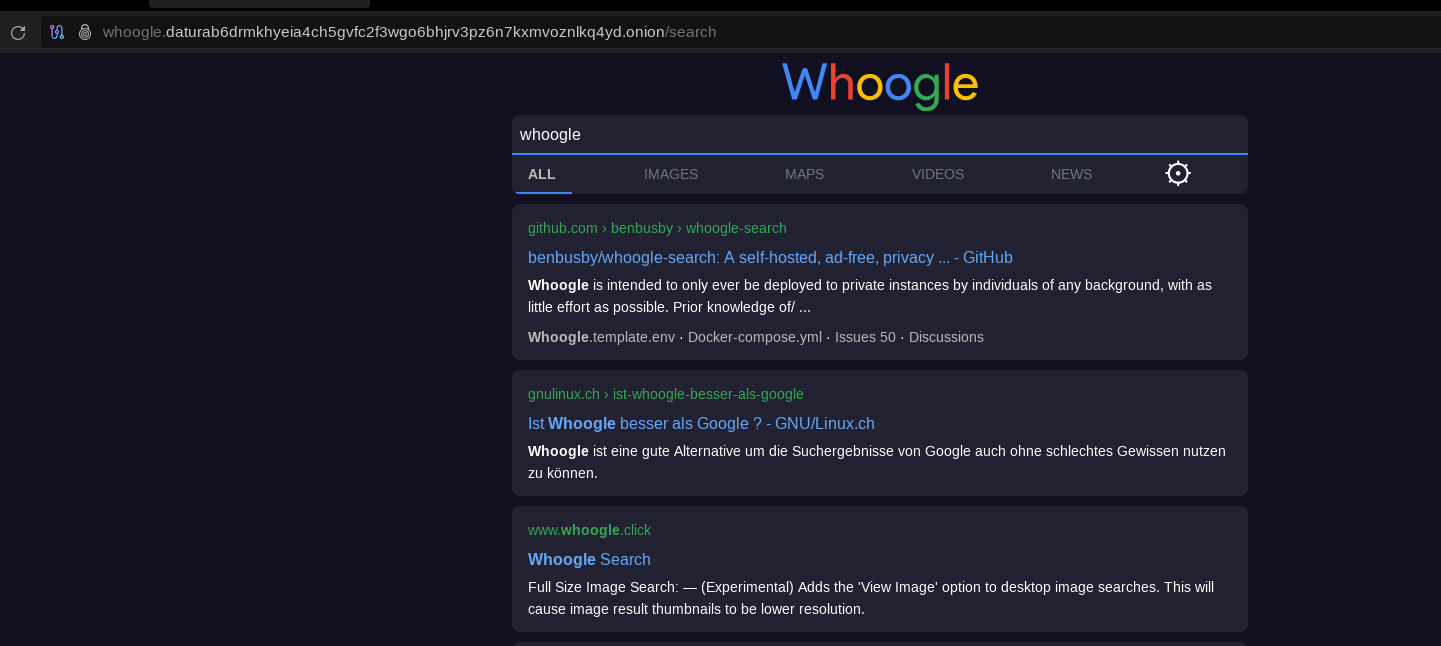
To contribute to the project, by listing your instance somewhere such as on the official github for whoogle, to do that, just open an issue on the official repository as shown here .
to have the service auto upgrade you can do as follows:
crontab -e
0 * * * * docker-compose -f /srv/whoogle-search/docker-compose.yml down ; git -C /srv/whoogle-search pull ; docker-compose -f /srv/whoogle-search/docker-compose.yml pull ; docker-compose -f /srv/whoogle-search/docker-compose.yml up -d
[ Datura Network ] [ /dev/pts/2 ] [~]
→ cronitor select
✔ docker-compose -f /srv/whoogle-search/docker-compose.yml down ; git -C /srv/whoogle-search pull ; docker-compose -f /srv/whoogle-search/docker-compose.yml pull ; docker-compose -f /srv/whoogle-search/docker-compose.yml up -d
----► Running command: docker-compose -f /srv/whoogle-search/docker-compose.yml down ; git -C /srv/whoogle-search pull ; docker-compose -f /srv/whoogle-search/docker-compose.yml pull ; docker-compose -f /srv/whoogle-search/docker-compose.yml up -d
Stopping whoogle-search ... done
Removing whoogle-search ... done
Removing network whoogle-search_default
Already up to date.
Pulling whoogle-search ... done
Creating network "whoogle-search_default" with the default driver
Creating whoogle-search ... done
----► ✔ Command successful Elapsed time 14.195s
Until there is Nothing left.
Donate XMR: 8AUYjhQeG3D5aodJDtqG499N5jXXM71gYKD8LgSsFB9BUV1o7muLv3DXHoydRTK4SZaaUBq4EAUqpZHLrX2VZLH71Jrd9k8
Contact: nihilist@nihilism.network (PGP)