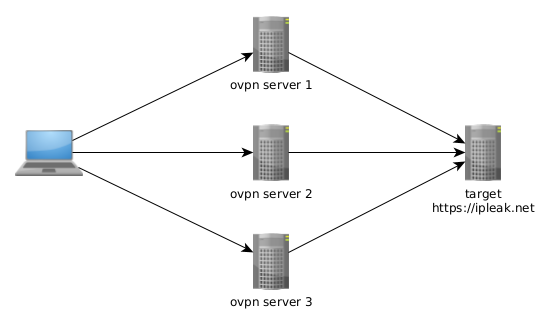
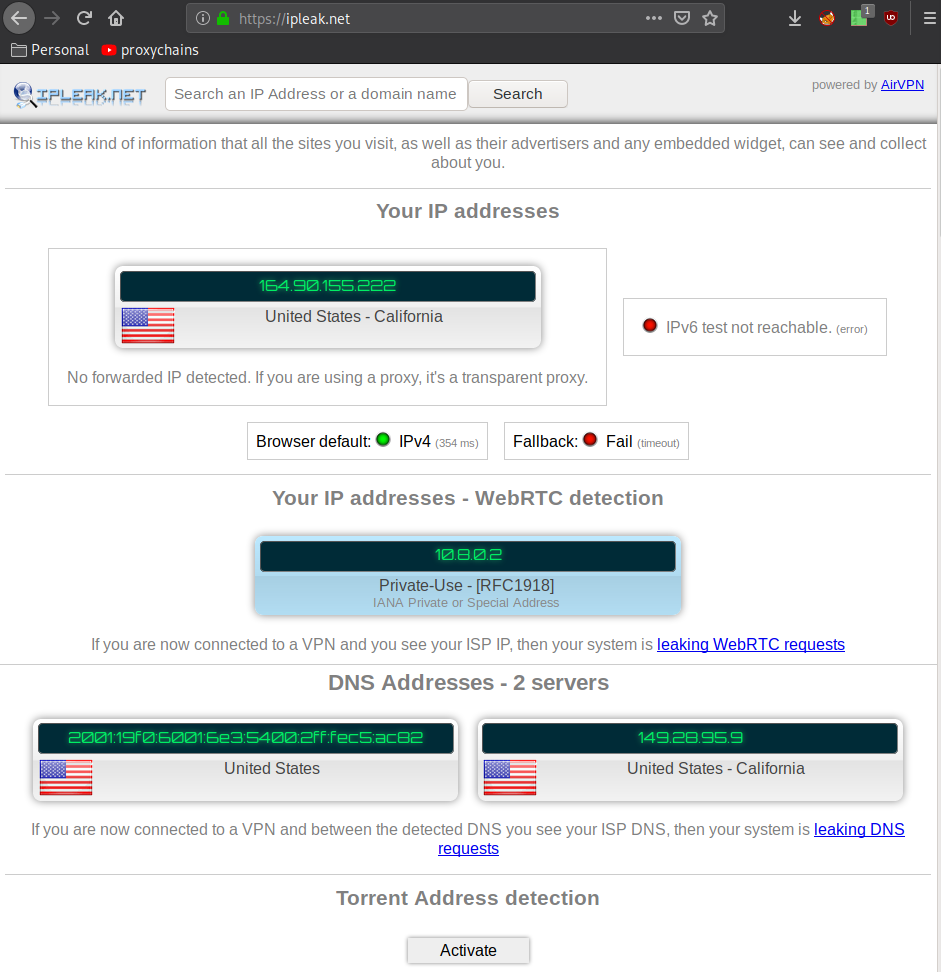
Getting the .ovpn file:
To get the ovpn file just use python's simplehttpserver module
root@debian-s-1vcpu-1gb-sfo3-01:~# ls -lash | grep ovpn
4.0K -rw-r--r-- 1 root root 2.7K Aug 12 15:41 nothing.ovpn
root@debian-s-1vcpu-1gb-sfo3-01:~# python -m SimpleHTTPServer 9099
Serving HTTP on 0.0.0.0 port 9099 ...
then just download it to your local machine:
[ 192.168.122.1/24 ] [ /dev/pts/7 ] [~]
→ wget http://164.90.155.222:9099/nothing.ovpn
--2020-08-12 18:43:48-- http://164.90.155.222:9099/nothing.ovpn
Connecting to 164.90.155.222:9099... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2764 (2.7K) [application/octet-stream]
Saving to: ‘nothing.ovpn’
nothing.ovpn 100%[=====================================>] 2.70K --.-KB/s in 0s
2020-08-12 18:43:48 (52.1 MB/s) - ‘nothing.ovpn’ saved [2764/2764]
[ 192.168.122.1/24 ] [ /dev/pts/7 ] [~]
→ ls -lash | grep ovpn
12K -rw-r--r-- 1 nothing nothing 9.3K Aug 3 12:18 nihilist777.ovpn
4.0K -rw-r--r-- 1 nothing nothing 2.7K Aug 12 16:41 nothing.ovpn
And that's it, you may now use the .ovpn file with whatever client you wish for example openvpn or your distro's built in vpn utility:
[ 10.99.99.1/24 ] [ /dev/pts/22 ] [~]
→ sudo openvpn nothing.ovpn
[sudo] password for nothing:
2022-01-09 16:52:42 Unrecognized option or missing or extra parameter(s) in nothing.ovpn:18: block-outside-dns (2.5.5)
2022-01-09 16:52:42 OpenVPN 2.5.5 [git:makepkg/869f194c23ae93c4+] x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on Dec 15 2021
2022-01-09 16:52:42 library versions: OpenSSL 1.1.1m 14 Dec 2021, LZO 2.10
🔐 Enter Private Key Password: *********
Now if you want the openvpn service to start at bootup, do the following:
[ 10.8.0.5/24 ] [ /dev/pts/22 ] [~]
→ sudo vim /etc/systemd/system/vpn.service
[ 10.8.0.5/24 ] [ /dev/pts/22 ] [~]
→ cat /etc/systemd/system/vpn.service
[Unit]
Description=VPN
After=network-online.target
Wants=network-online.target
[Service]
Type=simple
ExecStart=/usr/sbin/openvpn /home/nothing/nothing0mainpc.ovpn
ExecStop=kill -9 $(pidof openvpn)
Restart=always
[Install]
WantedBy=multi-user.target
[ 10.8.0.5/24 ] [ /dev/pts/22 ] [~]
→ systemctl daemon-reload
==== AUTHENTICATING FOR org.freedesktop.systemd1.reload-daemon ====
Authentication is required to reload the systemd state.
Authenticating as: nothing
Password:
==== AUTHENTICATION COMPLETE ====
And then from there you can start and stop your vpn like so:
[ 10.8.0.5/24 ] [ /dev/pts/22 ] [~]
→ sudo systemctl start vpn
[ 10.8.0.5/24 ] [ /dev/pts/22 ] [~]
→ sudo systemctl stop vpn
And to enable it at each system bootup:
[ 10.8.0.5/24 ] [ /dev/pts/22 ] [~]
→ sudo systemctl enable vpn
Created symlink /etc/systemd/system/multi-user.target.wants/vpn.service → /etc/systemd/system/vpn.service.
To avoid your vpn config from routing all traffic to the server, just add this line in the .ovpn file:
pull-filter ignore redirect-gateway